Ensure CWE Compliance and Strengthen C/C++ Code Security using CppDepend
Introduction
In the world of software development, adhering to secure coding practices is crucial for protecting applications and systems from potential threats. Achieving CWE (Common Weakness Enumeration) compliance is an essential step in this process. CPPDepend offers a robust solution for C/C++ developers to ensure CWE compliance, effectively strengthening code security and overall software quality.
In this guide, we will explore the benefits of using CPPDepend for CWE compliance, including its powerful features for identifying and mitigating vulnerabilities, enhancing code quality, and promoting secure coding practices in your C/C++ projects.
Using CWE Rules in CppDepend
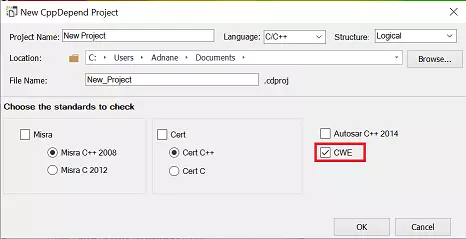
When you create a new CppDepend Project, a pop-up will appear displaying all the coding standards you would like to include in your analysis. To include CWE coding standards, check the CWE option.
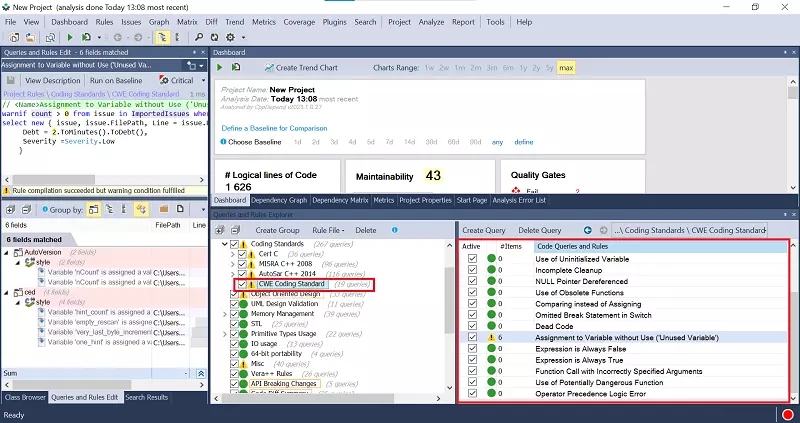
After analyzing your project, Navigate to the Queries and Rules Explorer section, and select the CWE Rules from the left-hand menu (Highlighted in red in the image below). This will display all the related CWE rules on the right. Upon clicking a Rule, the corresponding CQLinq query and the relevant source code will be automatically generated. Additionally, the Metrics View section provides a visualization of the issue's location and significance.
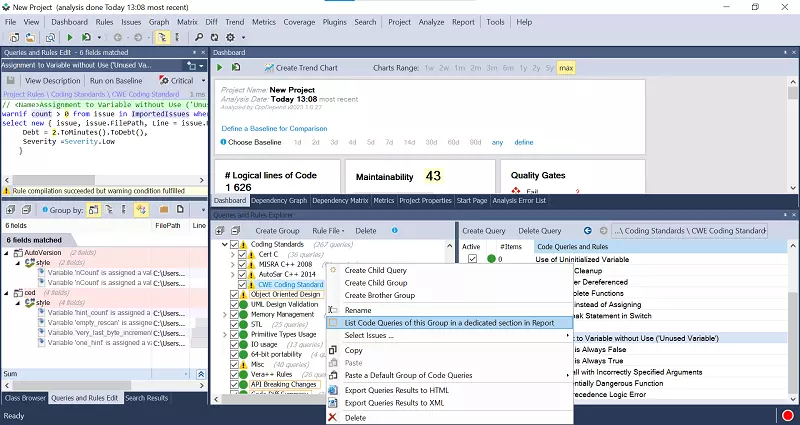
Incorporating CWE Rules into the HTML Report
To include the CWE rules in the generated HTML Report (available in the DevOps Edition), simply right-click on the CWE group and select "List Code Queries of this Group in a dedicated section in Report."
List of CWE Rules
-
Buffer Copy without Checking Size of Input ('Classic Buffer Overflow'):
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck"
&& (issue.Type=="bufferAccessOutOfBounds" || issue.Type=="possibleBufferAccessOutOfBounds"
|| issue.Type=="insecureCmdLineArgs"|| issue.Type=="invalidscanf") select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Divide By Zero:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="zerodiv" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Unchecked Error Condition:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="zerodiv" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Declaration of Catch for Generic Exception:
This coding standard is computed with the following query:
warnif count > 0
from m in Methods where !m.IsEntryPoint
&& m.IsUsing("Keywords.generic_catch".AllowNoMatch()) select m -
Improper Release of Memory Before Removing Last Reference ('Memory Leak'):
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && (issue.Type=="memleak" || issue.Type=="memleakOnRealloc"
|| issue.Type=="publicAllocationError"|| issue.Type=="leakNoVarFunctionCall") select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Double Free:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="deallocDealloc" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Use of Uninitialized Variable:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="uninitvar"
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 10.ToMinutes().ToDebt(),
Severity =Severity.High
} -
Incomplete Cleanup:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="resourceLeak" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
NULL Pointer Dereferenced:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="nullPointer" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Use of Obsolete Functions:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CLang" && issue.Type=="warn_deprecated" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Comparing instead of Assigning:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="CLang" && issue.Type=="warn_unused_comparison" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Omitted Break Statement in Switch:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="Clang" && issue.Type=="warn_unannotated_fallthrough" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Dead Code:
This coding standard is computed with the following query:
warnif count > 0
from issue in ImportedIssues where issue.ToolName=="Clang" && issue.Type=="warn_unreachable" select
new { issue,issue.FilePath,Line=issue.BeginLine} -
Assignment to Variable without Use ('Unused Variable'):
This coding standard is computed with the following query:
warnif count > 0 from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="unreadVariable"
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 2.ToMinutes().ToDebt(),
Severity =Severity.Low
} -
Expression is Always False:
This coding standard is computed with the following query:
warnif count > 0 from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="knownConditionTrueFalse"
&& issue.Description.Contains("always false")
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 2.ToMinutes().ToDebt(),
Severity =Severity.Low
} -
Expression is Always True:
This coding standard is computed with the following query:
warnif count > 0 from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="knownConditionTrueFalse"
&& issue.Description.Contains("always true")
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 2.ToMinutes().ToDebt(),
Severity =Severity.Low
} -
Function Call with Incorrectly Specified Arguments:
This coding standard is computed with the following query:
warnif count > 0 from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="preprocessorErrorDirective"
&& issue.Description.Contains("Wrong number")
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 2.ToMinutes().ToDebt(),
Severity =Severity.Low
} -
Use of Potentially Dangerous Function:
This coding standard is computed with the following query:
warnif count > 0 from issue in ImportedIssues where issue.ToolName=="CppCheck" && issue.Type=="dangerousUsageStrtol"
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 2.ToMinutes().ToDebt(),
Severity =Severity.Low
} -
Operator Precedence Logic Error:
This coding standard is computed with the following query:
warnif count > 0 from issue in ImportedIssues where issue.ToolName=="CppCheck" && (issue.Type=="clarifyCalculation"
|| issue.Type=="clarifyCondition")
select new { issue, issue.FilePath, Line = issue.BeginLine ,
Debt = 2.ToMinutes().ToDebt(),
Severity =Severity.Low
}




